
1. Introduction to Cloud Computing
Cloud Computing refers to both the applications delivered as services over the Internet and the hardware and systems software in the datacenters that provide those services. The datacenter hardware and software is what we will call a Cloud (M Armbrust et al, 2009). Cloud computing is relatively new concept and it has become popular recently. Cloud leverages virtualization technology and in the essence of cloud computing there is a logical separation between different nodes, each node appears as a different physical machine to the user. Unlike grid computing, it makes several distributed computers connected together to form a big logical computer which can handle large amount of data and computation. In case of cloud computing the virtualization technology makes it possible to have each node appear as separate physical machine allowing user to load custom software and operating system on each node and configure custom rules for each node.
The idea of cloud computing is evolved from parallel processing, distributed computing and grid computing. There is a bit similarity between them but they work differently. Although cloud computing is an emerging field of computer science, the idea has been around for a few years. It's called cloud computing because the data and applications exist on a "cloud" of Web servers. To simplify the concept, cloud computing can be defined as simply the sharing and use of applications and resources of a network environment to get work done without concern about ownership and management of the network’s resources and applications (M.‐S. E Scale, 2009). According to Scale, with cloud computing, computer resources for getting work done and their data are no longer stored on one’s personal computer, but are hosted elsewhere to be made accessible in any location and at any time.
2. Related Technology Comparison
2.1. Grid computing
Aform of distributed computing and parallel computing, whereby a 'super and virtual computer' is composed of a cluster of networked, loosely coupled computers acting in concert to perform very large tasks
2.2. Utility computing
The packaging of computing resources, such as computation and storage, as a metered service similar to a traditional public utility, such as electricity.
2.3. Autonomic computing
Computer systems capable of self‐management.
3. General mechanism
Cloud computing using information technology as a services over the network. The concept generally encompasses of Infrastructure as a service (IaaS), Platform as a service (PaaS) Hardware as a Service (HaaS) and Software as a service (SaaS). It can be the ability to rent a server or servers and run a geophysical modeling application available anywhere. It can be the ability to (S Rupley, 2009) rent a virtual server, load software on it, turn it on and off at will, or clone it to meet a sudden workload demand. It can be storing and securing large amounts of data that is accessible only by authorized applications and users. It can be supported by a cloud provider that sets up a platform with the ability to scale automatically in response to changing workloads. It can be using a storage cloud to hold application, business, and personal data. And it can be the ability to use a handful of Web services to integrate photos, maps, and GPS information to create a front page in customer Web browsers.
In a cloud computing system, there is a significant workload shift. Local computers no longer have to run applications. The network of computers that make up the cloud handles them instead. In this situation the demand of hardware and software on the user's side is decreased. Let the cloud take care of it. The only thing that local computers should aware is the interface software that will run the application. Today’s, a Web Browser such as Mozilla FireFox and Internet Explorer 8 is widely use as an interface software in cloud computing system.
The truth is, internet users already used some form of cloud computing. If they have an e‐mail account with a Web‐based e‐mail service like Hotmail, Yahoo! Mail or Gmail, then they had some experience with cloud computing. Instead of running an e‐mail program on a local computer, user will log in to a Web e‐mail account remotely. The software and storage for the account does not exist in the local computer it is on the service's computer cloud.
4. Key characteristic of Cloud Computing
Currently, there is no standard definition or specification for Cloud Computing. It may take some time to define the key characteristics of Cloud Computing based on practices in the field (L‐J Zhang and Q Zhou, 2009). Based on practices in the areas of service provisioning and solution design, the following two key enabling technologies could play a vital role in this revolutionary phase of cloud computing:
4.1. Virtualization technology
Virtualization technology works to handle on how the image of the operating system, middleware, and application pro‐created and allocated to a physical machine or part of the server stack away. The virtualization technology can also help reuse licenses of operating systems, middleware, or software applications, once a subscriber releases their service from the Cloud Computing platform.
4.2. Service‐Oriented Architecture (SOA).
A service‐oriented architecture is essentially a collection of services. These services communicate with each other. The communication can involve either simple data passing or it could involve two or more services coordinating some activity. Some means of connecting services to each other is needed. The evolution of a system or software architecture is now moving towards services oriented, unlike several decades ago most of the application is stand alone and purposely for single use. Recently, the gigantic growth of the internet user and internet technology availability the use of software now can be rented. Giant company such as Google, Microsoft, Sun or even Amazon have this capability provide software services instead of selling the software directly to user. The SOA is software or system architecture that addressing componentization, reusability, extensibility, and flexibility. These entire characteristic is a fundamentals need for company that are looking for reducing cost and opt to rent instead of purchase.
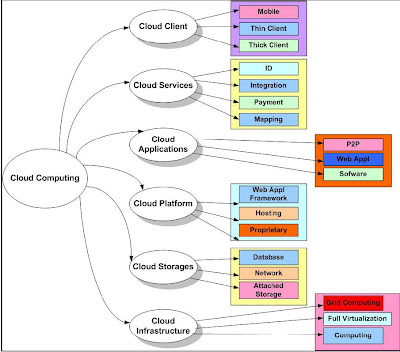
5. Architectural layers of cloud computing
Cloud computing can describe services being provided at any of the traditional layers from hardware to applications. In practice, cloud service providers offer a services that can be grouped into several architectural layers (B.P Rimal and E Choi (2009) and sometime refer as style in Cloud Computing environment (Z Shuai et al , 2010) , Infrastructure as a service (IaaS) and Platform as a service (PaaS) and Software as a service (SaaS).
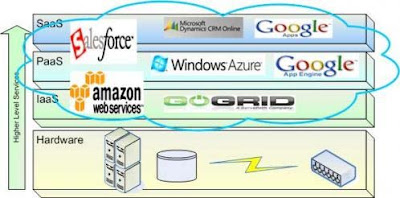
5.1. Software as a service (SaaS)
Software as a service features a complete application offered as a service on demand. A single instance of the software runs on the cloud and services multiple end users or client organizations. The most widely known example of SaaS is salesforce.com, Gmail, Google Calendar, Payroll, HR, CRM, Sugarm CRM, IBM Lotus Live and it also include other examples is services including email and word processing.
The companies below are already established in SaaS business. These companies charge their customers a subscription fee and in return host software on central servers that are accessed by the end user via the internet.
5.1.1. Salesforce.com
5.1.2. Google
5.1.3. NetSuite
5.1.4. Taleo
5.1.5. Concur Technologies
5.2. Platform as a service (PaaS)
Platform as a service encapsulates a layer of software and provides it as a service that can be used to build higher‐level services. It involved, middleware, Integration, Messaging, Information, Connectivity setup. The good example is a Google Apps engine which serves applications on Google’s infrastructure. PaaS services like this can provide a powerful basis on which to deploy applications, however they may be constrained by the capabilities that the cloud provider chooses to deliver. A freedom of development is limited.
The following companies are some that have developed platforms that allow end users to access applications from centralized servers using the internet. Next to each company is the name of their platform.
5.2.1. Google ‐ Apps Engine
5.2.2. Amazon.com ‐ EC2 and S3
5.2.3. Microsoft ‐ Windows Live
5.2.4. Terremark Worldwide ‐ The Enterprise Cloud
5.2.5. Salesforce.com ‐ Force.com
5.2.6. NetSuite ‐ Suiteflex
5.2.7. Mosso ‐ Mosso, a division of Rackspace
5.2.8. Metrisoft ‐ Metrisoft SaaS Platform
5.3. Infrastructure as a service (IaaS)
Infrastructure as a service delivers basic storage and compute capabilities as standardized services over the network. Servers, storage systems, switches, routers, and other systems are pooled and made available to handle workloads that range from application components to high‐performance computing applications. Example IaaS in market today is IBM Blue house, VMWare, Amazon EC2, Microsoft Azure Platform, Sun Parascale and more.
Below are companies that provide infrastructure services:
5.3.1. Google ‐ Managed hosting, development environment
5.3.2. International Business Machines (IBM) ‐ Managed hosting
5.3.3. SAVVIS ‐ Managed hosting
5.3.4. Terremark Worldwide ‐ Managed hosting
5.3.5. Amazon.com ‐ Cloud storage
6. Type of Cloud Computing mode
The boundaries of cloud computing can be divided into three, public cloud, private cloud and hybrid cloud (B.P Rimal and E Choi , 2009). The following Figure 3 below will illustrate the cloud computing boundaries.
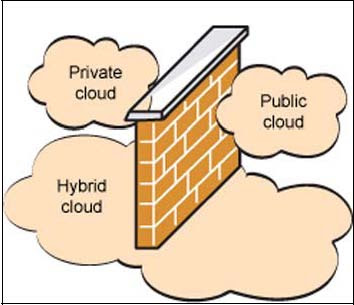
6.1. Public Cloud
Open for use by general public. Exist beyond firewall, fully hosted and managed by the vendor. User can be and individuals, corporations and others. Amazon's Web Services and Google App engine are good examples of public cloud computing.
6.2. Private Cloud
Work within the boundaries (firewall) of the organization. All of the (B Prentice, 2008) advantages of public cloud with one major difference; it has to be managed by the enterprise and has control over resources. It is more secure as they are internal to organization. Comparing with the public cloud the development of private cloud requires hardware investments and need to hire in‐house expertise. It will drag the cost exceeding the public cloud.
6.3. Hybrid Cloud
Can be defined as the combination of private and public cloud but still has the firewall to distinguish between them.
7. Security issues in Cloud Computing
There are many companies who are into the market offering various ranges of services on Cloud Computing. Cloud computing enables users and developers to utilize services without expert knowledge and control over the technology infrastructure that supports them. But as more and more information on individuals and companies is placed in the cloud, concerns are beginning to grow about just how safe an environment it is. Organization such as European Network and Information Security Agency (ENISA), the Cloud Security Alliance (CSA) and Information Systems Audit and Control Association (ISACA), are among of the leading organizations shaping the future of Cloud Computing Security.
The Cloud Security Alliance publish an important document publicly, "Top Threats to Cloud Computing V1.0.". While security environment of Cloud Computing is uncertain and declare as unsecured environments, organizations like the CSA work diligently on defining the standards, describing best practices, and highlighting the top risks and threats (CSA, 2010). There were seven threats of Cloud Computing security according to the report:
7.1. Abuse and nefarious use of cloud computing.
The easiness of registering for IaaS solutions and the relative anonymity they offer attracts many a cyber criminal. IaaS offerings have been known to host botnets and/or their command and control centers, downloads for exploits, Trojans, and others. There is a numerous of ways in which cloud capabilities can be misused such as possible future uses include launching dynamic attack points, CAPTCHA solving farms, password and key cracking and more.
7.2. Insecure interfaces and APIs.
As software interfaces or APIs are what customers use to interact with cloud services, those must have extremely secure authentication, access control, encryption and activity monitoring mechanisms , especially when third parties start to build on them. The keys to solving those problems are a thorough analysis of the interfaces and quality implementation of the security mechanisms.
7.3. Malicious insiders.
The malicious insider threat is one that gains in importance as many providers still don't reveal how they are hired people, how they grant them access to assets or how they monitor them. In this case, transparency is vital to a secure cloud offering, along with compliance reporting and breach notification.
7.4. Shared technology issues.
Sharing infrastructure is a way of life for IaaS providers. Unfortunately, the components on which this infrastructure is based were not designed for that. To ensure that customers don't thread on each other's territory, monitoring and strong compartmentalization is required, not to mention scanning for and patching of vulnerabilities that might jeopardize this coexistence.
7.5. Data loss or leakage
This is one of the top concerns for businesses, because they not only stand to lose their reputation, but are also obligated by law to keep it safe. There are a number of things that can be done to prevent such occurrences, from consistent use of encryption and quality disaster recovery to contractual specifications regarding backup and secure destruction practices.
7.6. Account or service hijacking.
The attacker can gather information, change data, falsify transactions, and also redirect your clients to illegitimate sites. In today’s technology and network environment, it only takes a credible phishing site or a good social engineering approach, and the keys to your castle have changed hands. Strong authentication techniques, security policies and monitoring should prevent this from happening.
7.7. Unknown risk profile
Security should always in the upper portion of the priority list. Code updates, security practices, vulnerability profiles, intrusion attempts, all of these things that should always be kept in mind. Never do just the minimum security actions, be ready to go the extra (security) mile.
8. Advantage and disadvantage
Cloud computing seems to offer some incredible benefits for communicators: the availability of an incredible array of software applications, access to lightning‐quick processing power, unlimited storage, and the ability to easily share and process information. All of this is available through your browser any time you can access the Internet (R Maggiani, 2009). Minimize infrastructure risk, when pushing an application out to the cloud, scalability and the risk of purchasing too much or too little infrastructure becomes the cloud provider’s issue. It is no more machine dependent issues to the company. Then the cost will automatically reduced, in the past, companies would sometimes buy costly servers before they knew how much space they would need. Now businesses can save money by paying companies, such as Amazon, for storage, and they only need to pay for the storage that they use. With cloud computing, users no longer need to upgrade the server, buy a new server, upgrade storage, and operational costs of other inefficient. Internet access is so easy to find.
Despite these advantages, it has its own disadvantages which must be considered. Users are subject to terms and conditions imposed by service provider; carefully need to understand the terms and condition before sign up with cloud computing services. It maybe invaded your data privacy and risks your highly confidential data and resources. The other issues might be, the reliability of the communication between client and service provider. The dependency of internet connection is too high. Internet connectivity isn’t completely stable and reliable for cloud computing to be completely accessible anywhere at all time. Last but not least, the most important part is security issues. Security is always a concern, especially when it involved data storage. How secure is your data when it is not stored in your physical location. Only one place data is really safe and secure, and that's within your own storage facility with proper backups and safely stored.
9. Conclusion
Creating a so‐called Cloud Computing platform is easy as long as it can enable sharing of at least one of the resources. However, building a unified, scalable and reusable Cloud Computing architecture to support sharing of all types of resources still faces challenges in the areas of technology breakthrough and best industry practices (L‐J Zhang and Q Zhou, 2009).
No matter what your requirements are, the cloud services make sense. If it is not a complete switch to a cloud service, possibly a partial switch might work. In the simple manner, cloud computing refers to the storage of data on servers instead of on individual hard drives.
However, we also still have to be careful about our personal data, the number of people who store personal data on servers that can be accessed from internet has grown. Millions of users upload personal data such as emails, photographs and even data work to sites owned by other companies such as Google. One of the reasons why you should not use the web application is because you are not in control. Using the web application is as dangerous as a proprietary program. Do computing on your own computer with an application that supports freedom.
References:
R Maggiani. (2009). “Cloud Computing Is Changing How We Communicate”. In Proceedings of Professional Communication Conference, 2009, Waikiki, Hawaii. IPCC 2009. IEEE International
Michael Armbrust, Armando Fox, Rean Griffith, Anthony D. Joseph, Randy H. Katz, Andrew Konwinski, Gunho Lee, David A. Patterson, Ariel Rabkin, Ion Stoica and Matei Zaharia (2009). “Above the Clouds: A Berkeley View of Cloud Computing”. Retrieved 04 04, 2010, from http://www.eecs.berkeley.edu/Pubs/TechRpts/2009/EECS-2009-28.html
B Prentice. (2008). “Cloud Computing and Open Source: An Industry-Altering One-Two Punch”. Retrieved 04 04, 2010, from http://staff.ee.sun.ac.za/~hgibson/docs/ubuntu/cloud_computing_and_open_sou_159058.pdf
S Rupley. (2009). “ Top Open-source Resources for Cloud Computing”. Retrieved 01 20, 2010, from http://gigaom.com/2009/11/06/10-top-open-source-resources-for-cloud-computing/
M.-S. E Scale. (2009). “Cloud computing and collaboration”. Retrieved 04 04, 2010, from http://www.emeraldinsight.com.libproxy.utem.edu.my/Insight/viewPDF.jsp?contentType=Article&Filename=html/Output/Published/EmeraldFullTextArticle/Pdf/2390260903.pdf
Z Shuai, Z Shufen, C Xuebin, H Xiuzhen (2010), “ Cloud Computing Research and Development Trend". In Proceeding of Second International Conference on Future Networks, 2010. ICFN '10. Sanya, Hainan, China
L-J Zhang and Q Zhou (2009),"CCOA: Cloud Computing Open Architecture". In Proceeding of IEEE International Conference on Web Services, 2009. ICWS 2009.
B.P Rimal and E Choi (2009), "A Conceptual Approach for Taxonomical Spectrum of Cloud Computing". In Proceedings of the 4th International Conference on Ubiquitous Information Technologies & Applications, 2009. ICUT '09. Fukuoka, Japan
Cloud Security Alliance CSA (2010),"Top Threats of Cloud Computing V1.0", Retrieved 04 04, 2010, from http://www.cloudsecurityalliance.org/topthreats































Hello,
Excellent information about cloud hosting
If explained in a layman's term, cloud server hosting is a technology which allows you to store your data over the internet.
Cloud Hosting India
Very informative! Thank you very much!
no deposit bonus forex 2021 - takipçi satın al - takipçi satın al - takipçi satın al - takipcialdim.com/tiktok-takipci-satin-al/ - instagram beğeni satın al - instagram beğeni satın al - google haritalara yer ekleme - btcturk - tiktok izlenme satın al - sms onay - youtube izlenme satın al - google haritalara yer ekleme - no deposit bonus forex 2021 - tiktok jeton hilesi - tiktok beğeni satın al - binance - takipçi satın al - uc satın al - finanspedia.com - sms onay - sms onay - tiktok takipçi satın al - tiktok beğeni satın al - twitter takipçi satın al - trend topic satın al - youtube abone satın al - instagram beğeni satın al - tiktok beğeni satın al - twitter takipçi satın al - trend topic satın al - youtube abone satın al - instagram beğeni satın al - tiktok takipçi satın al - tiktok beğeni satın al - twitter takipçi satın al - trend topic satın al - youtube abone satın al - instagram beğeni satın al - perde modelleri - instagram takipçi satın al - instagram takipçi satın al - cami avizesi - marsbahis
I think this is the best I've seen till now. Thank you so much for sharing.
crm software providers in Madhapur hyderabad
Awesome blog! crm software providers in madhapur hyderabad
Thank you for sharing wonderful information with us to get some idea about it.
oracle soa 12c training
oracle soa 12c training
SaaS & Cloud Data Backup Solutions vCloud Tech provides SaaS and Cloud backup and recovery services that utilizes encrypted cloud-based technologies to secure your data.
PERDE MODELLERİ
Numara onay
mobil ödeme bozdurma
nft nasıl alınır
Ankara evden eve nakliyat
Trafik sigortası
DEDEKTOR
web sitesi kurma
Ask romanlari
smm panel
smm panel
https://isilanlariblog.com
İNSTAGRAM TAKİPÇİ SATIN AL
hirdavatciburada.com
beyazesyateknikservisi.com.tr
servis
tiktok jeton hilesi
Good content. You write beautiful things.
hacklink
hacklink
vbet
taksi
mrbahis
mrbahis
sportsbet
korsan taksi
sportsbet